Platform Capabilities
Three core capabilities that provide continuous threat exposure management across your critical infrastructure
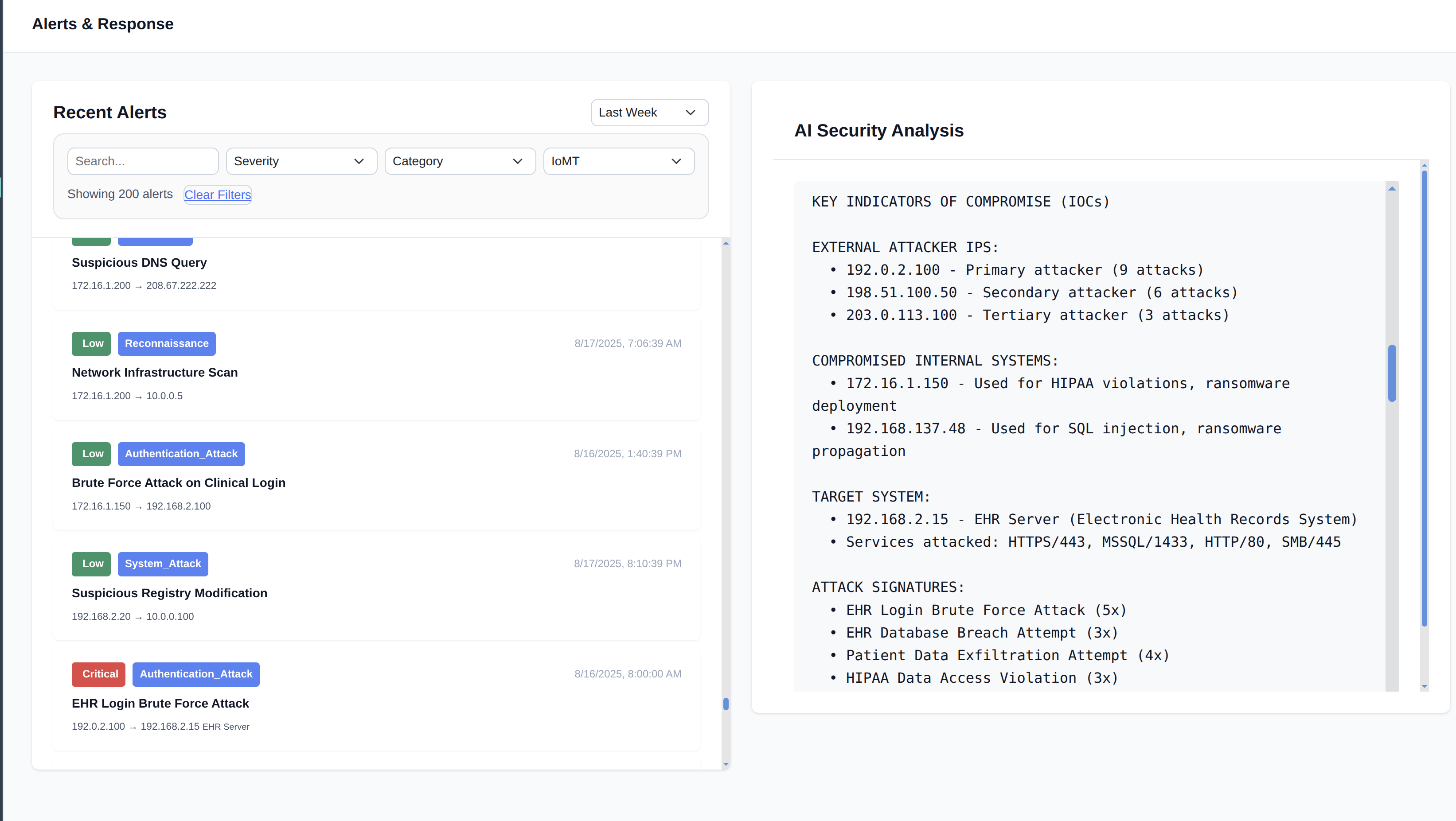
Threat Detection
Advanced Detection for ICS/OT Threats
Detect sophisticated threats targeting industrial protocols (Modbus, DNP3, OPC, etc.) with advanced behavioral analytics trained on ICS attack patterns. Identify anomalies in process behavior and lateral movement before they impact operations.
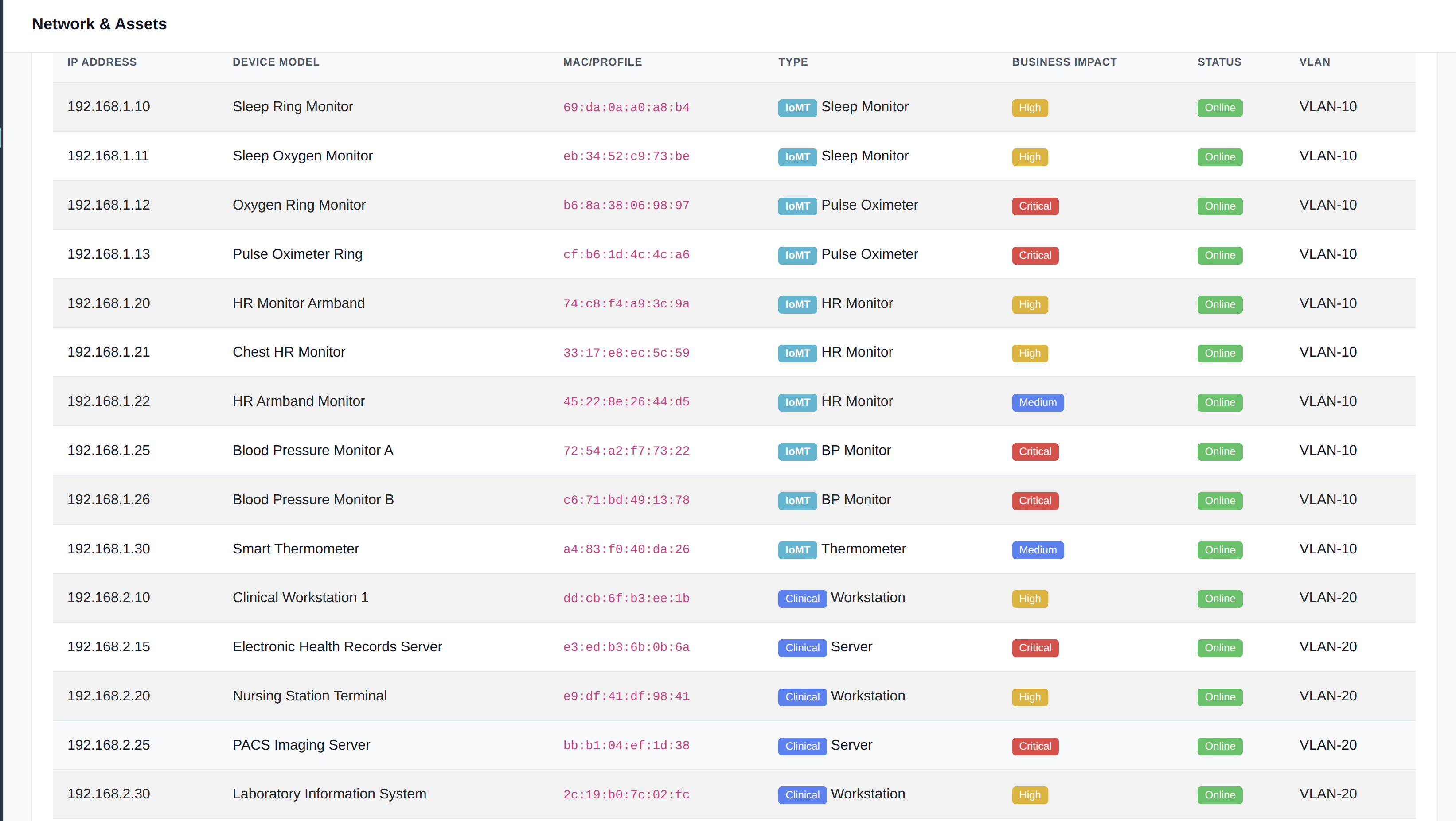
Asset Discovery
Complete Visibility Across IT/OT Environments
Automatically discover and inventory every asset across your converged IT/OT network. Our platform identifies PLCs, SCADA systems, HMIs, and industrial devices while mapping relationships and dependencies critical to your operations.
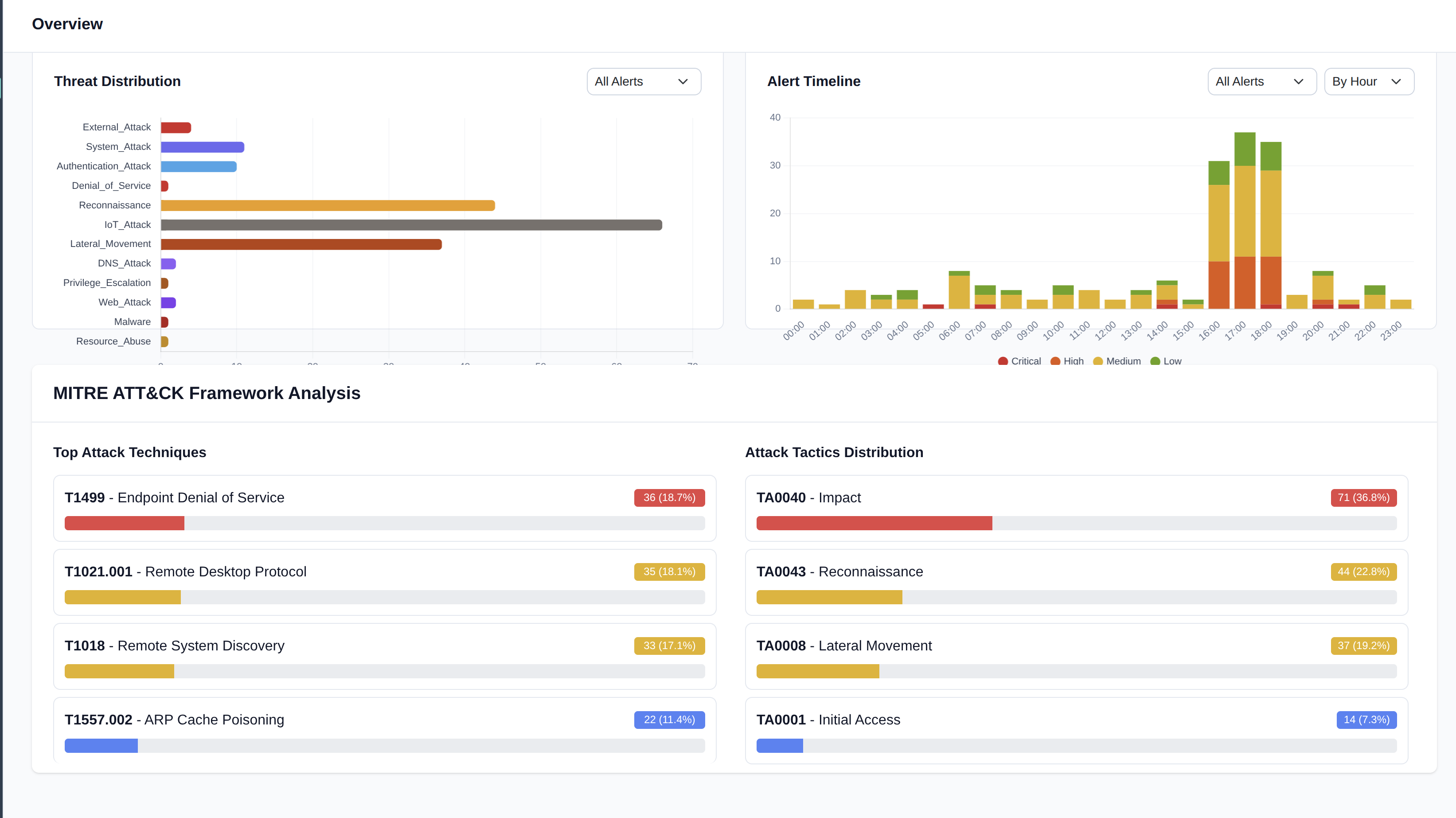
Vulnerability Management
Continuous Assessment & Risk-Based Prioritization
Continuously assess vulnerabilities across legacy and modern systems without disrupting operations. Intelligent risk scoring prioritizes remediation based on exploitability, asset criticality, and operational impact, not just CVSS scores.